Business Email Compromise (BEC) is a direct attack that exploits and targets individuals through social engineering tactics, such as impersonating an executive, vendor, or associate or stealing credentials in order to get an associate to share company information.
Also known as spear phishing – BEC directly targets a specific individual or group of individuals within an organization. Fund transfers or sensitive information is requested from employees who believe the requests are authentic and legitimate. These types of attacks can be extremely sophisticated and are constantly evolving in order to make them harder to detect.
Seventy-one percent of organizations experienced attempted or actual Business Email Compromise (BEC) in 2022.
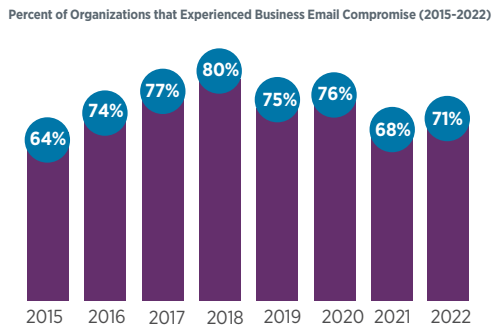
*Source: AFPonline.org
Different Types of Email Compromise:
- Spoof Email
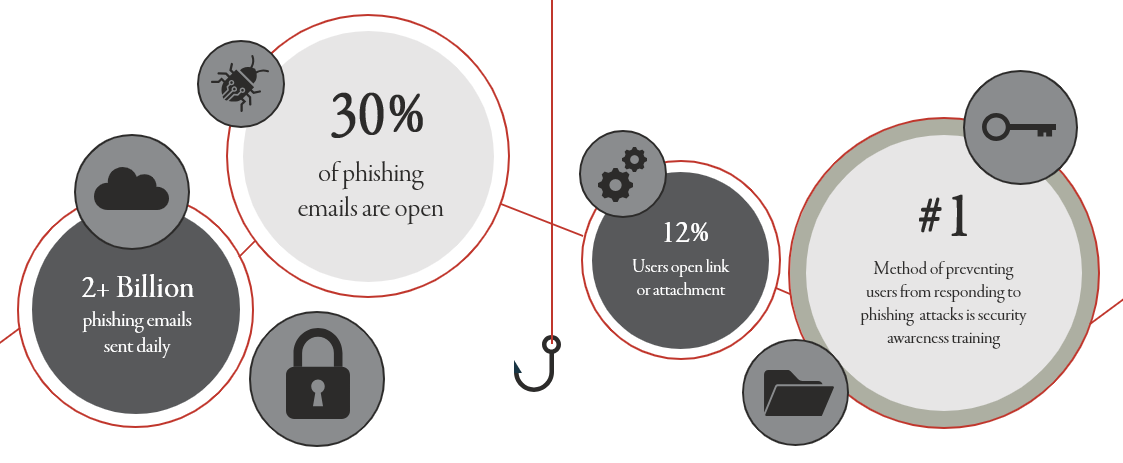
This is a technique used in phishing and span attacks, tricking the user into thinking that a message has come from a known entity they know or trust, enticing the user to click a malicious link, open malware attachments, or even send sensitive data. 73% of organizations experience email account and website spoofing. - Domain Lookalike
Fraudsters create look-alike domains, one which is nearly identical but slightly altered, in order to confuse users into believing they have reached a legitimate site. Visiting these sites can lead a user to give sensitive information or download malware. 57% of organizations experience domain lookalike. - Compromised Email Account
Fraudsters take over a legitimate email account and send fraudulent “change of payment” instructions to innocent organizations and users. The hacker obtains access by mining the associate’s contact list for company vendors, partners and suppliers and then messages the associate requesting payments be sent to a fake account that has been created by the cyber criminal.
What to Look For: An Example of Business Email Compromise
Notice the following in the example of the email below.
- The email address has been slightly altered. (original email was )
- The company name is misspelled in the first sentence (Thomson instead of Thompson).
- The wording is a bit awkward and words are misspelled (planed instead of planned)
- The note indicates a “revised invoice” with updated bank information.
- Note the usage of words such as “kindly” and “regards” which often indicate fraudulent activity.
Please note: These have been simulated as an example.

- Never trust an email that includes updated bank account information. Always call and verify details with every transaction.
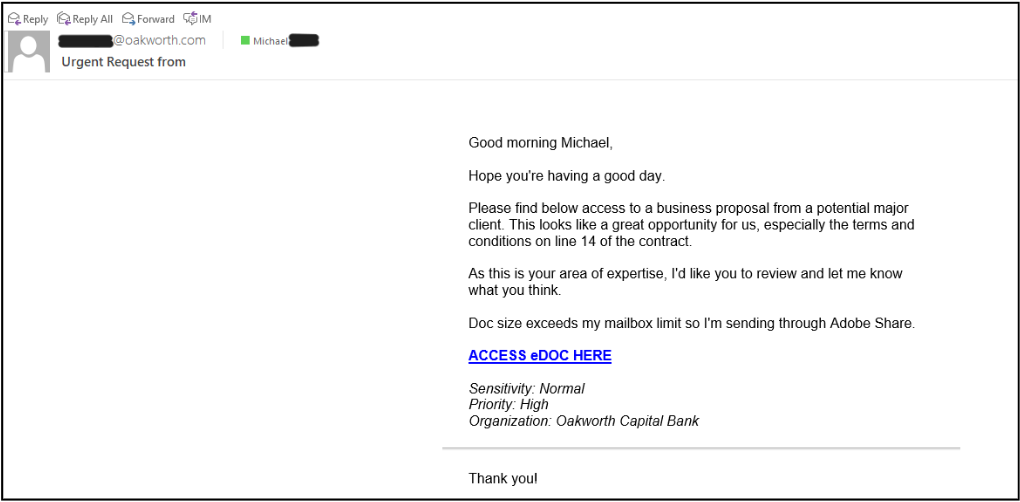
Here is another email of Lookalike Domain that appears to come from inside an organization:
- Note the “Urgent Request” in the subject line and the “High” priority.
- Note the attachment.
5 Tips from Oakworth’s Treasury Management Team Around BEC Fraud Prevention
- Slow Down
Look for a spoof on an email account or website. Senders will forge email header elements to trick users into thinking they are using a trusted source. Is the sending email address from a legitimate source? - Pay Attention to URLs, Domains
What is the exact domain or URL? Fraudsters build look-alike domains to confuse users into believing that they have reached a legitimate site. Visiting these sites may lead to web traffic diversion and/or malware delivery. An example might be “Miccrosoft.com” instead of “Microsoft.com”; “Arnazon.com” instead of “Amazon.com.” - Take Caution
if any information has changed, such as a routing number or banking institution. Fraudsters will sometimes use compromised email accounts to send fraudulent “change of payment” instructions to potential victims. Fraudulent emails may contain attachments or links that send users to illegitimate websites, new routing numbers or payment portals. Anytime you are notified of a change in an email call the known number (NOT the number listed in the email) to verify. - Look for Key Words
Fraudulent emails often contain certain words and phrases that may serve as indicators that something is not quite right, such as “urgent action required” “official notice” and “kindly reply as soon as possible.” Misspelled words and odd grammar is often found as well.
The good news is that there has been a slight downward trend in payments fraud activity since 2018, likely because more and more companies are putting preventative measures in place and regularly training their associates on how to detect different types of fraud. However, 65% of organizations are still being targeted; two out of three companies continuing to be victims of fraudulent attacks.
Payment fraud prevention is the key to safer and healthier business growth. Talk to an Oakworth treasury management advisor today for more information.
Prevention in Action
Read more about how Oakworth was able to help JetRight Aerospace Holdings prevent a fraudulent payment via Business Email Compromise, HERE.
Note: This article is part of a special content series on Corporate Fraud Prevention. Also check out:
- What is Payments Fraud?
- 12 Key Solutions to Help you Protect Your Business Against Fraud
- The Benefits of Positive Pay
WATCH OUR RECORDED EVENT:

American businesses will lose an average of 5% of their gross revenues to fraud. The biggest contributing factor? Not having the right internal, standardized procedures in place in order to prevent fraud from occurring. Join the Oakworth Treasury Management team for a detailed discussion so you can better protect your business on the front end.
What is Corporate Fraud? | Amelia Ricks CTP
Treasury Management Advisor, Central Alabama Market
Who are Fraudsters? What are Attacks? | Tyler Fruland
Treasury Management Specialist, Middle Tennessee Market
Corporate Fraud Solutions | Jaye B. Patterson
Treasury Management Specialist, South Alabama Market
This information is being provided for informational and educational purposes and is not meant to be taken as specific advice. All decisions regarding the legal implications of these strategies should be discussed with your advisors before being implemented.



